PrintNightmare Playbook
07 Jul 2021Patches and additional configuration changes (to prevent trivial UNC bypass) are required to mitigate this RCE. Fun.
- Identify the list of vulnerable systems. You’ll need to provide a domain user (not administrator) account username and password.
(grab code from https://github.com/byt3bl33d3r/ItWasAllADream) docker run -it itwasalladream -u user -p password -d domain 192.168.5.0/24You’ll get output like:
[itwasalladream] INFO - 192.168.5.7 is vulnerable over MS-PAR. Reason: Host attempted to grab DLL from supplied share [itwasalladream] INFO - 192.168.5.7 is vulnerable over MS-RPRN. Reason: Host attempted to grab DLL from supplied share - Apply all patches on all systems. Reboot.
- If patches cause machines to misbehave, you probably should panic and apply mitigations.
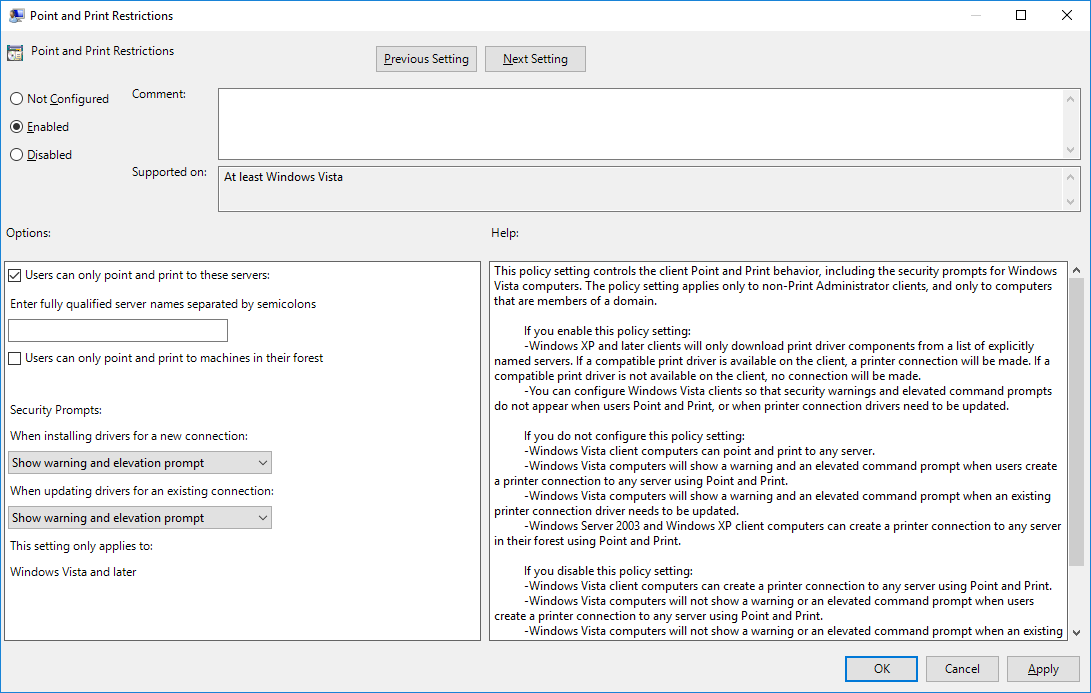
- Push Group Policy to disable Point and Print:
- Group Policy Management Editor window, click Computer Configuration, click Policies, click Administrative Templates, and then click Printers.
- Right-click Point and Print Restrictions, and then click Edit.
- Point and Print Restrictions dialog box, click Enabled.
- (enabled) Users can only point and print to these servers: (blank)
- Security Prompts: “Show warning and elevation prompt” for both.
- On standalone servers/workstations:
(from elevated command prompt) reg add "HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows NT\Printers\PointAndPrint" /v RestrictDriverInstallationToAdministrators /t REG_DWORD /d 1 /f - Verify list of vulnerable computers is empty.
docker run -it itwasalladream -u user -p password -d domain 192.168.5.0/24
See also: